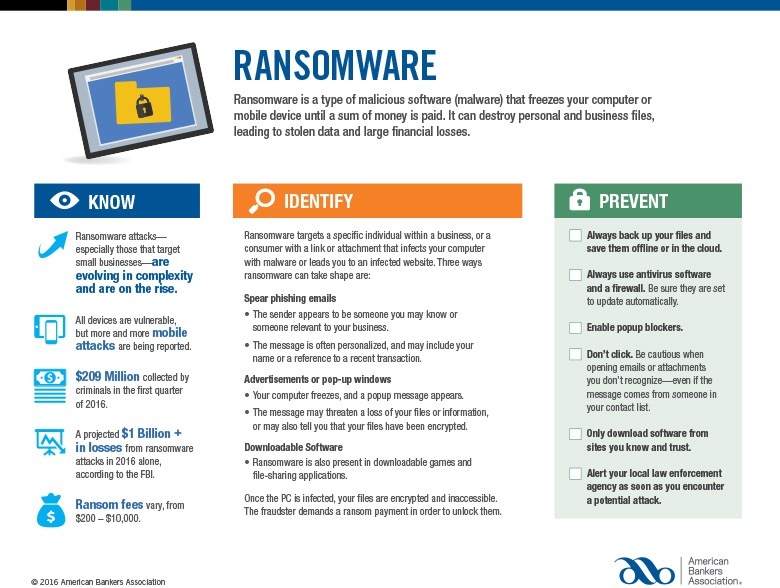
Ransomware.
Of all the cyber threats businesses and governments face today, none creates a bigger, colder collective shiver than this.
Here’s how it works: someone installs malware on your computer or mobile device that then makes it unusable until a ransom demand is paid. In the meantime, personal and business data can be destroyed or stolen, leading to financial devastation.
Unfortunately, too many of us respond after the fact instead of planning ahead.
“Be educated on the latest schemes and scams to avoid becoming a victim,” said Jeff Taylor, head of commercial fraud forensics for Regions Bank. “Almost all ransomware events begin with a phishing email or accessing a malicious link that allows the fraudster to infect your system with malware. Take your time, investigate the email address of the sender, and be leery of unrequested links or attachments.”
There is good news, however. Let’s start with the Department of Homeland Security and the Department of Justice, which have a website (StopRansomware.gov) that can help you mitigate these threats.
And the American Bankers Association has created a Ransomware toolkit, which includes the MAP (Mitigate, Assess and Prepare) plan for those who suspect they have been targeted by ransomware:
Mitigate Damage from Ransomware
- Isolate the affected device(s) – Determine which systems are infected. Temporarily take the network offline if possible. Disconnect all infected or potentially infected components from the network to contain the spread.
- Do not erase or attempt to fix corrupted files – This could disrupt the “crime scene” and hinder investigative and recovery efforts.
- Do not power down device – Ransomware artifacts and evidence could be lost if components are completely powered down. Virus spread vs. evidence retention should be weighed by senior leadership. If unable to disconnect devices from network, power them down to contain the infection.
Assess Damage
- Triage systems for restoration and recovery – First, identify and prioritize critical systems for recovery. Image system and affected devices. Collect all relevant logs or indicators of compromise (e.g., suspicious commands) and preserve for analysis.
- Evaluate whether backup data is available – Ensure backups are not connected to the corrupted system. To limit chances of reinfection, consider restoring data from the oldest version of a backup, preferably older than 100 days.
Prepare Response
- Engage law enforcement in consultation with your legal department – Contact the FBI and Secret Service. Law enforcement may provide intelligence that could decrypt your systems. They may also assist in navigating regulatory reporting requirements.
- Decide whether to pay the ransom – In consultation with senior leadership, legal department, and other stakeholders, decide whether to pay.
- Determine whether to hire or consult with an external forensic group – To assist in recovery, potential payment, and further mitigation.
- Notify customers and appropriate federal and state bodies – Contact the appropriate regulatory bodies about breach of customer data. Identify affected customers for further data breach notifications. File a Suspicious Activity Report with FinCEN. Follow your state’s data breach notification requirements.
“Unfortunately, any business, regardless of size, can become a ransomware victim,” Taylor said. “Preparing an event response plan is a critical step in the recovery process. Knowing who to call, how to reach them, and the role of each participant will provide a better roadmap to recovery during a very stressful time.”
Ransomware remains big business, with criminals pulling in hundreds of millions of dollars from victims who were unprepared. Once again, the ABA provides useful information for identifying and stopping ransomware.
The information presented is general in nature and should not be considered, legal, accounting or tax advice. Regions reminds its customers that they should be vigilant about fraud and security and that they are responsible for taking action to protect their computer systems. Fraud prevention requires a continuous review of your policies and practices, as the threat evolves daily. There is no guarantee that all fraudulent transactions will be prevented or that related financial losses will not occur. Visit regions.com/STOPFRAUD or speak with your Banker for further information on how you can help prevent fraud.